Spring Boot Interview Question – Securing Sensitive Fields in Records
discussion, code samples , design and more.
Scenario
Your team is modernizing a legacy system by migrating DTOs to Java records for immutability and reduced boilerplate.
Everything seems fine — until production logs show passwords and API keys in plaintext.
Clearly, something needs to change.
You are tasked with designing a system so that sensitive fields:
Are never logged in plaintext.
Are persisted safely in the database.
Work across multiple entities and layers.
Can leverage Spring Boot + JPA.
Can handle legacy systems where field names may vary.
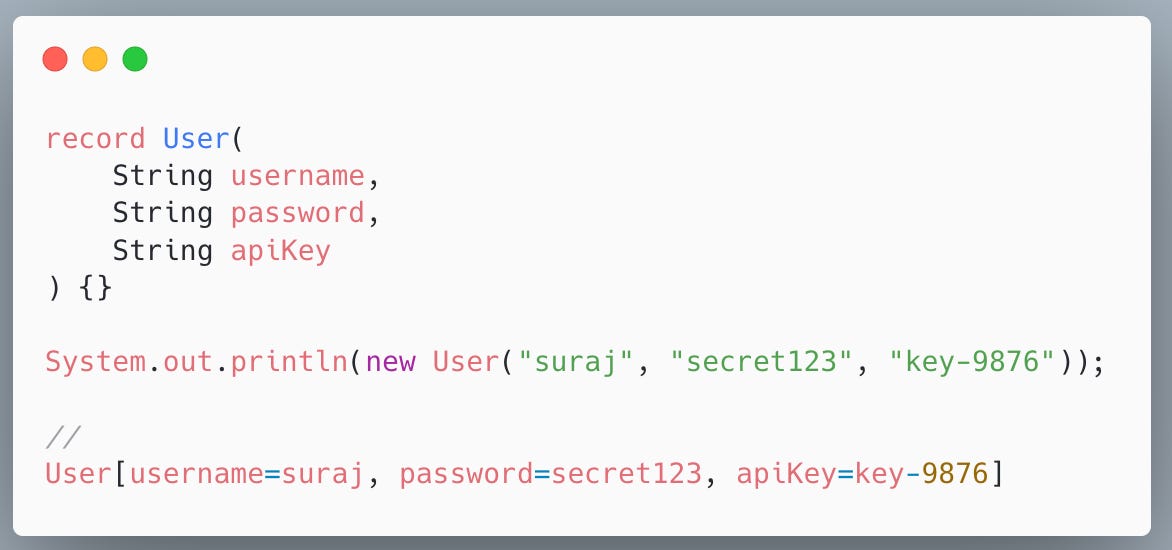
Example Code:
Sensitive data leaks immediately.
How would you ensure sensitive fields are masked in logs and safe in the database, without overriding every record’s
toString()?
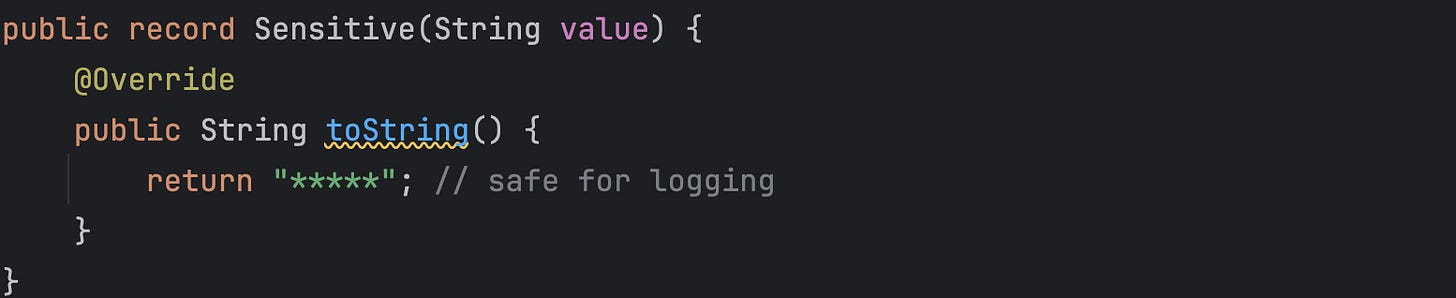
We can do type-level masking, i.e. wrap sensitive values in a domain type with record:
Records will use this type for sensitive fields:
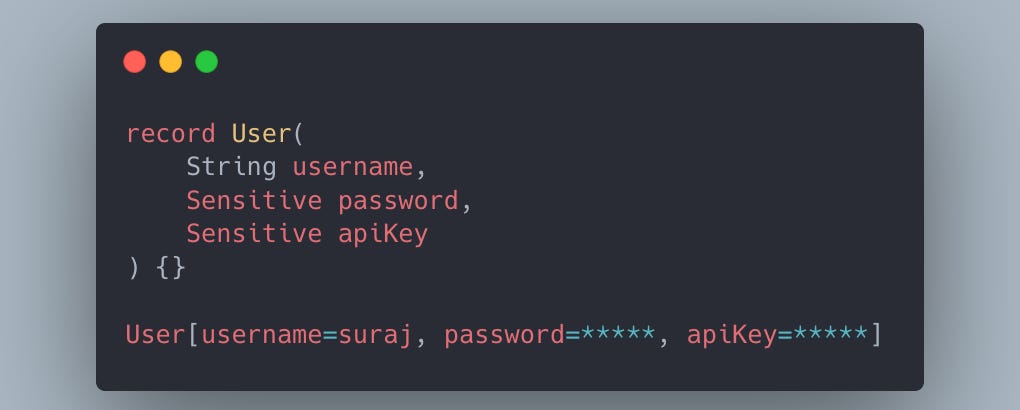
If we log a user object, it will be masked for sensitive fields. Safe, consistent, and independent of field names.
That handles the domain object , How about JPA layer ? How do we ensure writes to the database is actual value, while reads are masked?
⏰ Ends today: $18/year for Java & Spring Boot (40% off)
Join 4000+ subscribers and level up your Spring & backend skills with hand-crafted content — no fluff.
Currently, we have covered 39 real world use case based interview problems, and another 16 problems are in progress. Our initial goal is to complete at least 100 problems in the upcoming months.
Not convinced? Check out the details of the past work
Persistence with JPA
Spring Boot/Hibernate needs to know how to persist Sensitive. We need to create a converter that does to and from for database columns, and allows us to simply annotate Sensitive fields.